There’s been a lot of talk about how a backdoor sneaked into a compression library, but what’s just as fascinating is how, over time, the author managed to gain trust and become one of the trusted programmers.
This is an evolving situation and will be updated as more information comes to light. You can contact me on Twitter if you have more information to share
Last update: 9 AM UTC (April 1 2024)
TLDR;
All those interaction illustrated in this article look innocent on the surface. But when connecting the dots, this looks like a long-term scheme to insert a backdoor into the Xz library. “Outsiders” pushing the main maintainer to step down, their unusually professional GitHub interactions, linking projects and PR, in a strategy to build trust and facilitate their goal.
With many very good articles already done by other cyber security researchers about the reverse engineering and technical aspect I want to focus on the other side which is in my opinion even more important, the social engineering aspect. Over several months, the suspicious account meticulously submitted pull requests to various projects. This slow, steady strategy subtly weakened numerous security measures that otherwise could have thwarted the backdoor attempt.
Timeline
Year 2021, the Enigmatic Journey of a Rogue Developer
Two suspected accounts were created on GitHub. The nickname JiaT0218 itself comes from a pull request changing the e-mail from the maintainer of the project https://github.com/JiaT75/oss-fuzz/commit/6403e93344476972e908ce17e8244f5c2b957dfd
- JiaT75 on January 26 2021
- JiaT0218 on May 16 2021 (potential sock-puppet account, never used)
In one of the commit a name is specified: “Jia Cheong Tan”. This is most likely a fake name.
In the early part of 2021, JiaT75 was active, making multiple contributions to private repositories. Given the private nature of these contributions, we’ll refrain from speculating.
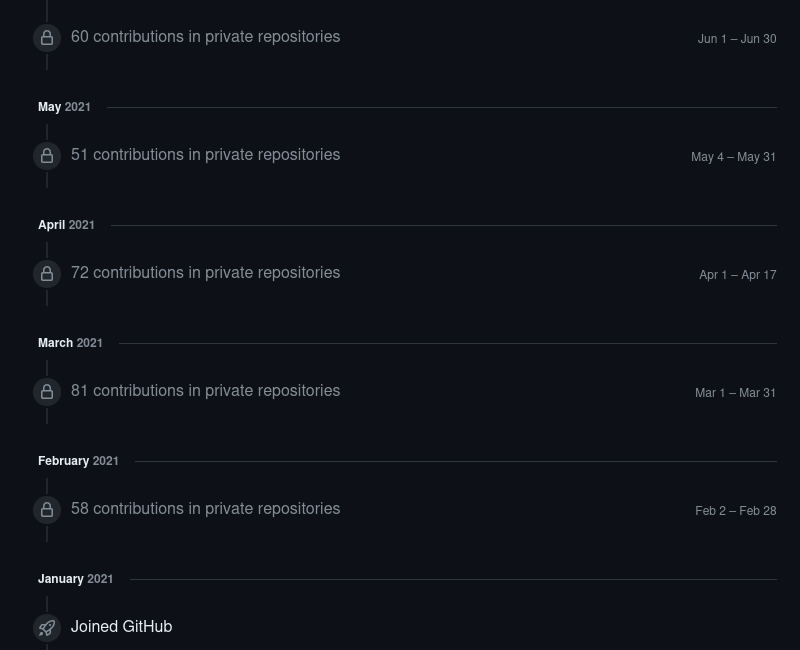
The first public contribution didn’t emerge until September, marked by a pull request to libarchive (view it here). The same week, several open source project are cloned and the amount of contribution starts to ramp up: pull requests, code reviews in multiple projects.
A specific pull request caught our eye: GitHub pull request #1595 in the libarchive repository. In it, JiaT75 attempted to introduce a range of unusual dependencies. When questioned, he dismissed it as a harmless error. While beginners often We see again and again the same pattern. Simily inconent changes that put togheter form a deeper webmistakenly add strange dependencies, we must keep in mind the possibility of malicious intent.
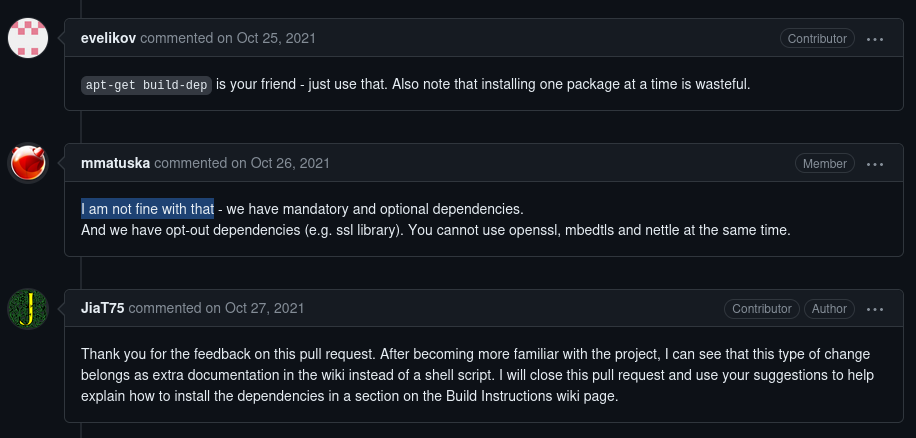
The pull request at seatest #28 is also intriguing because it appears to introduce a pattern that will become later a recurring tactic: claiming to fix errors by merely bypassing or eliminating specific compilation flags and settings.
In another pull request (libarchive #1609), the author casually describes it as “Added error text to warning when untaring with bsdtar,” but subtly switches out a secure print function for an unsafe variant. These pull requests are meticulously prepared, often referencing issues, having easily readable descriptions while glossing over some of the more dubious changes made to the code.
As the new year approaches, we’re looking at a GitHub account that’s bustling with activity from numerous contributions. And maybe it sounds a bit out there, but I’d estimate that 70% of folks glancing at an account like this would rate it as a solid, reputable one. All of this in less than a year.
Year 2022, The Stealth Campaign Against a Lone Guardian
This year is interesting, because JiaT75 delivers one of his initial patches to Xz, and we see a new figure: “Jigar Kumar.” Kumar not only intensifies the pressure on “Lasse Collin” Xz’s existing maintainer but also urges him to include more contributors. Although it’s regrettably typical for open-source projects to face demands for features or additional efforts from volunteers, the mix of Kumar’s persistent pressure on this specific project and his absence from any other project activities raises red flags especially in the light of another similar account “Dennis Ens”.
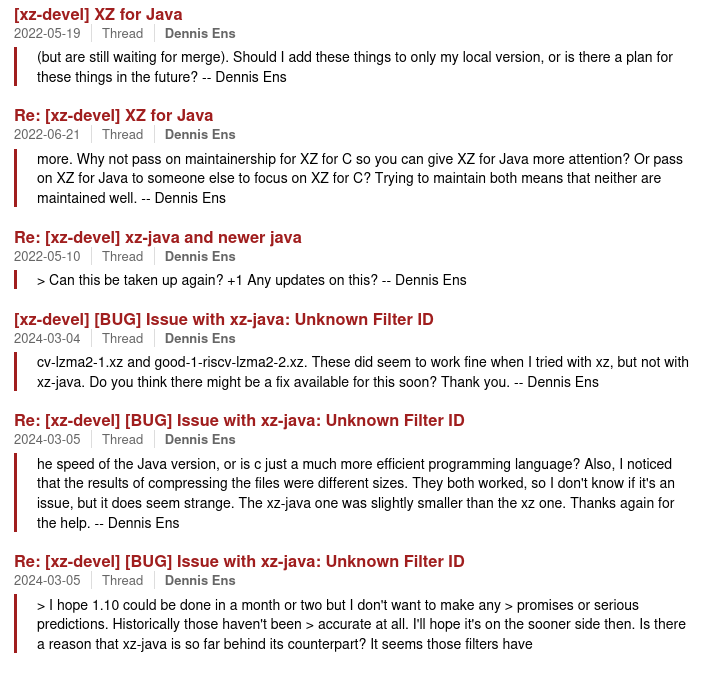
Imagine being the only person maintaining a widely used library and feeling the heat from subtle hints to quit, while also dealing with a “helpful” new contributor, our providential suspect JiaT75. These accounts kept nudging him to leave the project and concentrate on the Java library instead.
Finally on October 18 2022, JiaT75 joins the Tukaani organization responsible for overseeing the development of Xz. The name organization can be a bit misleading here JiaT75 and Lasse Collin are the only two members.
We also have a report for one of the person working in the translation team to be contacted by JiaT75 thanking them for their contributions and building more trust in the broader open source community.

2023
Throughout 2023, JiaT75 laid the groundwork for inserting a backdoor. He began by redirecting the Xz project’s bug and security issue reporting email to his own. Instead of altering an existing repository directly, he updated a template. You can see the pull request here.
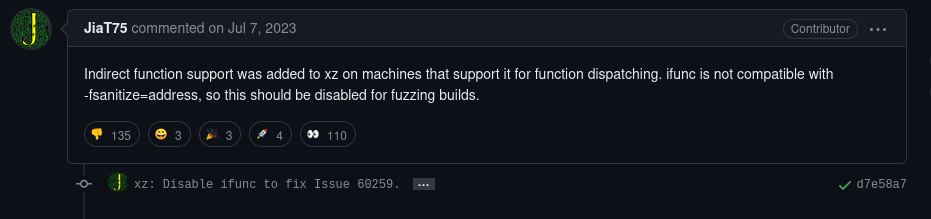
The next pull request the now infamous: “Disable ifunc to fix Issue 60259,” is available at https://github.com/google/oss-fuzz/pull/10667. I won’t comment further; you can read and judge for yourself.
If I made any mistake or if you have more information, feel free to contact me on Twitter
Sources
This report stands on the shoulders of giants. For a deeper dive, I highly recommend exploring these excellent reports.
- https://boehs.org/node/everything-i-know-about-the-xz-backdoor
- https://www.openwall.com/lists/oss-security/2024/03/29/6
- https://bsky.app/profile/filippo.abyssdomain.expert/post/3kowjkx2njy2b
On a side note, the picture used in the profile seems to be coming from some clip art library